Diving into the crypto world, have you ever wondered what is hashing in cryptocurrency? It’s a cornerstone, a kind of digital magic happening beneath the shiny surface of every bitcoin transaction. Let’s cut through the complex jargon. Hashing keeps your digital money safe and sound from the bad guys. It’s like a secret code that no sneaky hacker can crack—at least not without a fight. When you hear ‘blockchain’, think hashing; they’re buddies working together to guard your precious coins. Stick around as we break down the big deal about hashing and show you how this crypto wizardry works.
The Essence of Hashing in the Cryptocurrency World
Exploring the Function and Role of Hashing
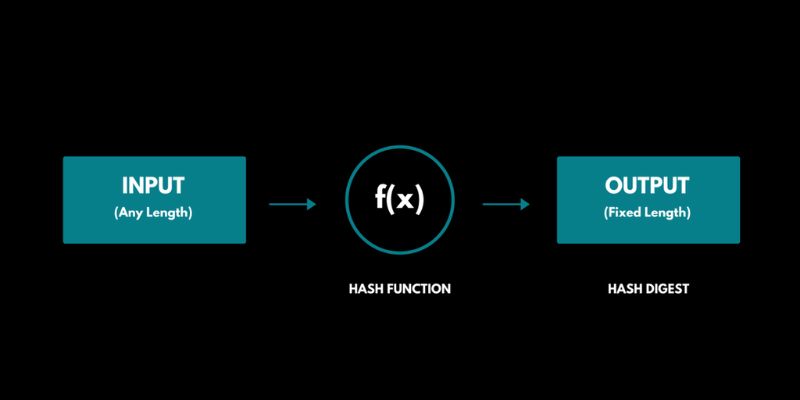
When we chat about crypto, we often hear about hashing. It’s like a secret code. But it’s really a way to keep everything safe and in order. A hash function is a special math problem. It takes data, like a message, and turns it into a string of numbers and letters. This string is a hash. Each hash is unique. Change a letter in the message, the hash changes a lot. Cryptographic hash functions are real important for this.
Now let’s say you’re playing with toy blocks. You make a cool tower. You list each block’s color and shape. That list keeps your tower safe. If a block changes, the list shows it. Hashing in crypto works like that list. It locks in data. It helps everyone agree on data without showing it all.

Understanding the Crucial Relationship Between Blockchains and Hashes
Blockchains and hashes are like best friends. They are always together. Think of a blockchain as a chain of toy blocks. Each block has a list of trade details. This list is the block’s hash. But it also remembers its last block’s hash. This links the blocks tight. When all blocks have correct hashes, you know the chain is good. No one messed with your toy blocks!
Remember when you traded cards with friends? You wrote down what you gave and got. That’s a bit like a blockchain. When people check trades on the blockchain, they look at block hashes. It’s quick! No need to read every trade. If hash one leads to hash two and so on, trades are fair and safe.
Hashes are key for mining in crypto like Bitcoin. Miners solve hard math to find new blocks. This game uses SHA-256, a secure hash algorithm. Miners guess numbers until they get the right hash. It’s like hitting the jackpot!
These math problems help keep things called coins safe. When you send a coin, the network checks the hash. Remember the toy blocks? Just like checking the list, they check the trade’s hash. If it fits, the trade is good. If it does not, something is wrong. And Ethereum uses a different hashing method, but the idea is the same.
So, hashing helps everyone agree without sharing all their details. It makes sure trades are true and safe. It’s a big part of why crypto can work. Hashing is a guard and a helper all in one. It’s not just math. It’s a way to make sure we can all play fair and have fun.
The Mechanics Behind Cryptocurrency Hashing
Diving into the Properties and Types of Hashing Algorithms
We know these unseen heroes as hash functions. They mix up any digital data into short, unique codes we call hashes. Think of a blending machine. You toss in fruit, and you get a smoothie. The same happens in crypto, but with numbers and letters, not fruits. This mix-up helps keep all digital currency deals safe and sound.
These hash functions follow strict rules. They must give a unique code for each unique set of data. If you change just one letter or number, you get a whole new hash. This is key for security in the crazy world of crypto. Can you tell two smoothies apart if they look the same? With hashes, every tiny difference matters.
Now, let’s peek into the different types of hashing algorithms. SHA-256 stars in the Bitcoin show. Ethereum picks another lead called Keccak. Each plays a part in making sure no one messes with your digital money.
Examining How Miners Utilize Hash Functions for Proof of Work
Now onto miners, the workers in the digital currency mines. What’s their shovel? The hash function! They use it all day to solve tricky math puzzles. This proof of work makes sure that adding new blocks of info is tough but checking them is easy.
Miners aim to find a special number, a nonce, that creates a hash that fits the rules of the network. Think of it as looking for a golden ticket in a mountain of chocolate bars. When a miner finds the golden ticket, bam! They add a block to the chain and earn some digital coins.
Mining isn’t just about luck. These miners have rigs, heavy-duty computers, that need to be fast and smart to win the race. The speed of their work is the hash rate. The faster the rate, the more puzzles they can solve.
They always stay secure by using hashes. It’s like making sure every step you take in the digital world leaves a footprint that can’t be erased or changed. Every single deal sticks like glue, thanks to these hashes.
So, next time you hear about Bitcoin or Ethereum, remember there’s a hash function working hard to keep everything in check. It’s all about mixing up that digital data to keep your coins safe and the blockchain happy!
Hashing: Ensuring Security and Integrity in Transactions
The Process of Verifying Transactions Using Hashes
Hash functions are key in making sure digital currency trades are real. When someone sends bitcoin to another, this action needs a legit check. A hash function steps in here. It mixes input data to make a short, unique output, the hash value. This hash is a string of numbers and letters, like a fingerprint for data. In the world of cryptocurrency, we call this process hashing. Each block in the blockchain has its own hash value, created from transaction details.
Let’s talk about bitcoin hashing. Say Alice sends some bitcoin to Bob. The network takes the transaction info and runs it through the hash function. Out comes a hash, which then goes onto the blockchain. It’s like sealing a letter with a unique stamp that says, “This is real.”
A change in the data sent through will make a new and different hash spit out. If a tricky person tries to change old transactions, the hash for that block changes too. This breaks the chain. Checks are constant; so bad changes are seen fast. Networks like Bitcoin use a hash function known as SHA-256. It’s super strong and keeps things secure.
The Significance of Hash Values and Digital Signature Hash in Cryptocurrency Security
Now, each trade also needs a digital signature hash. It proves a message came from the right sender. It’s also tied to the person’s secret key, so only they can make it. And each person has their own secret key, like a secret handshake. When they sign with it, others can check it with the public key. The digital signature hash is checked with the public key. If they match, it’s solid proof the signer is who they claim to be.
Hash values, like a treasure map, guide us in the transaction journey. They show the path of data, step by step. In cryptocurrency, this keeps our trades honest. Every block has its own hash value and links to the one before. This is thanks to hash pointers. They aren’t regular pointers! They not only say where to go next but also carry the hash of the block they point to. It’s like breadcrumbs but with secret codes that lead back to the start.
Cryptographic hash functions also allow miners to join the network game. They solve complex math puzzles using these hash functions. And it’s proof of their hard work, the proof of work that keeps the network moving smooth. They keep guessing until they find a hash that fits the network’s current puzzle. And boom! They can now add a new block to the chain and get new coins as a prize.
Knowing hash functions is like having a master key in the crypto world. It’s important because it locks our digital money tight and only lets the right people open it. So, when we talk about hashing and data security, it’s serious business. No one wants their funds taken by a sneak thief. Thanks to hashing, we all sleep a bit better at night, our digital wallets snug and secure.
Advanced Applications of Hashing in Cryptocurrency
Optimizing Hash Rate Performance in GPU Mining Operations
Hash rate means how fast we can mine crypto. A high hash rate means more chances to find the next block and get the reward. It is vital in mining crypto like Bitcoin. Every miner wants their GPUs to have the best hash rate. But it’s tricky to get that.
First, we need to pick the right GPU. One that’s powerful yet not too costly to run. We balance power usage with the hash rate. The goal is to get as many hashes per second as we can without spending too much on electricity.
The software we use matters too. We look for software that can squeeze the most out of our GPUs. Sometimes we need to update or tweak this software to keep the hash rate up.
We must keep our GPUs cool. Heat can slow down mining and even damage our gear. Proper cooling means our GPUs can work hard without getting too hot. We do this with fans, liquid cooling, or even special mining cases.
Improving hash rate is not set in stone. We always test and change things to find the best setup. This means our mining rigs always need attention to stay at the top.

Implementing Hash Functions within Smart Contracts and Decentralized Applications
Smart contracts use hash functions to keep deals secure and honest. They turn data into a unique code. This code, or hash, cannot be flipped back to the original data easily. This is good for keeping secrets safe.
Hashes also help us know if data stays the same. If the data changes, the hash will change. So, we can quickly check if someone messed with the data.
When a smart contract has a hash function, it can do cool things like create a digital signature hash. This is like signing a paper but for digital stuff. It shows that the person really agreed to the terms. This is key to trust in the digital world.
Blockchains and hashes also work together in decentralized apps, or DApps. Here, hashes help track changes and keep records straight. This helps us know that things are in order.
Remember when we talked about a hash value in transactions? That’s how we use hashes to make sure each transfer of crypto is true and hasn’t been changed. It’s a way to check and double-check every move in the crypto world.
You see, hash functions are more than just a tool. They are the guardians of trust in the blockchain universe. They keep our crypto trades honest. They help our smart contracts do what they should. They keep our digital signatures strong. In essence, they are what make our crypto world work well and safely.
In this post, we’ve covered the nuts and bolts of how hashing keeps the crypto world secure and running smooth. We peeked into how hashing works and its tie to blockchains—it’s the secret sauce that makes sure every transaction is safe and sound.
We also looked at the gears of crypto hashing, from the different kinds you’ll find to how mining folks keep the lights on with their proof of work. It’s all about making sure we can trust that our digital bucks stay in the right hands.
But it’s not just about keeping things under lock and key—hashing steps up the game for wicked fast GPUs and lays down the law in smart contracts. It’s the smarty-pants tech that makes sure deals go down without a hitch.
So, there you have it—hashing is like a superhero for your digital dough, and it’s here to stay. Whether you’re in it for the mining or just keeping your coins snug, hashing’s got your back!
Q&A :
What Is the Purpose of Hashing in Cryptocurrency?
Hashing serves several critical functions in cryptocurrencies. It is used to secure and validate the integrity of transaction data on the blockchain. Hashing transforms input data of any size into a fixed-size string of characters, which is typically a unique hash value. This process helps in the prevention of fraud and double-spending by ensuring that each recorded transaction is unalterable once it has been hashed and added to the blockchain.
How Does Hashing Ensure Security in Cryptocurrency Transactions?
Hashing enhances the security of cryptocurrency transactions by making it extremely difficult for malicious actors to manipulate the transaction data. Since the hash function generates a unique output for any given input, any modification to the transaction data would lead to a completely different hash value. This property, known as the avalanche effect, is critical because if the hash does not match the one stored on the blockchain, the network will reject the transaction.
Can Hashing in Cryptocurrency be Reversed?
Hashing functions in cryptocurrency are designed to be one-way operations, meaning that they are practically irreversible. This ensures that even if someone has access to the hash value, they will not be able to deduce the original input data. This one-way cryptographic function adds to the security and privacy of the transaction process, making it infeasible to reverse-engineer the hash.
What Role Does Hashing Play in the Mining Process?
In the context of cryptocurrency mining, hashing is pivotal. Miners compete to find a hash that matches the current target set by the network, which involves repeatedly hashing the block header with a nonce until the resulting hash is below the threshold. This process, known as proof-of-work, validates and adds new blocks to the blockchain. The first miner to find the correct hash is allowed to add the block to the blockchain and is rewarded with cryptocurrency.
Are All Cryptocurrency Hashing Functions the Same?
No, not all hashing functions used in cryptocurrency are the same. Different cryptocurrencies may use different hashing algorithms depending on their specific security requirements and performance considerations. For example, Bitcoin uses the SHA-256 hashing algorithm, while Ethereum initially used Ethash. Each algorithm has its unique properties and levels of complexity, which can affect the security and speed of transactions within their respective networks.



